Entra ID and Microsoft 365
Entra ID (formerly Azure AD) is Microsoft's cloud-based directory service. At a basic level, a directory service maintains lists of your users, and associated groups, as well as dealing with authentication. Entra ID is a foundational element of Microsoft 365 - any user of Microsoft 365 is actually listed in Entra ID.
From a technical perspective, while Microsoft 365 offers additional functionality on top of Entra ID, all access is through the Microsoft Graph API which gives a consistent way to access Entra ID and other Microsoft products.
For all intents and purposes, connecting 1Password SaaS Manager to Entra ID / Microsoft 365 is the same thing. If you only use Entra ID, then some data (for example, Sharepoint usage) will be empty.
Connect to Entra
SaaS Manager can use either OAuth 2.0 Authorization Code Flow or Client Credentials. Authorization Code Flow uses a consent screen to request access to specific scopes, while Client Credentials requires more involved and granular manual configuration in Entra.
Connect with Authorization Code Flow
By default, SaaS Manager uses Authorization Code Flow to connect to Entra. This ensures a secure sign-in experience and grants SaaS Manager permission to access the necessary Microsoft APIs on your behalf.
The default permissions that SaaS Manager requests are read-only.
You should connect to Entra ID with a user account that has at least the Directory Readers, Security Reader and Reports Reader roles.
If you enable Provisioning or Deprovisioning, you will also need the Directory Writers role.
Core scopes requested
| Scope | Reason |
|---|---|
| AuditLog.Read.All | This is used to read audit logs to extract last-login times for SAML2 enabled applications (only works with Entra ID P1 and P2). The Security Reader role enables this. |
| Directory.Read.All | Allows the SaaS Manager to read basic data in your organization's directory, such as users, groups and apps. It also allows us to retrieve information about the Office 365 licenses each user has been assigned. |
| Group.Read.All | SaaS Manager reads the names and IDs of security and Office 365 groups in your organization's directory. |
| GroupMember.Read.All | To show which users are members of each group, SaaS Manager needs to read the members of each group. |
| Reports.Read.All | Where audit log data is not available, SaaS Manager reads Microsoft Office 365 usage reports to return last used dates for applications like Teams, Yammer, OneDrive and SharePoint. The Reports Reader role enables this. |
| User.Read.All | SaaS Manager pulls a list of all Office 365 users, and basic profile properties like name, email, employee ID, job title and creation date. |
| User.ReadWrite.All | Required for provisioning and deprovisioning users. This needs the Directory Writers role. |
| DeviceManagementManagedDevices.Read.All | Used to return whether any devices are linked to a user, which can contribute to deciding if a Microsoft 365 E3 license is required. |
Application consent in Entra ID
Entra ID now offers a very comprehensive approach to OAuth application security. Recommended settings are to limit users' abilities to consent to OAuth applications. If you're an Entra Administrator, you can see the configuration your organization is using under Enterprise applications > Consent and permissions > User consent settings.
SaaS Manager requires a number of permissions to access resources in Entra ID and it's likely you will have Do not allow user consent or Allow user consent for apps from verified publishers, for selected permissions selected. In this case connecting SaaS Manager to Entra ID with a non-Entra administrator account will show a Need admin approval message.
To switch to using an Entra administrator account to make the connection, select Have an admin account? Sign in with that account.
SaaS Manager will not be granted the full access of your administrator account. Our access is limited to the OAuth scopes we request.
Approve the SaaS Manager application connection with a separate Entra admin account
If you want to use a different user account, for example a specific SaaS Manager 'service' account with just the Global Reader role, to connect from SaaS Manager to Entra ID, then you will still need an Entra Administrator to approve the SaaS Manager application.
The easiest way to do this is to ask an Entra Admin (who does not need to have a SaaS Manager account) to Select this admin login link.
This will initiate the process for approving the SaaS Manager connection in Entra ID.
On the permissions acceptance screen, you do not need to Consent on behalf of your organization. If you leave the box unchecked and a new connection is made, then the user must review the access SaaS Manager is requesting.
After you select Accept, the user will see a message from SaaS Manager that says "Request forwarding failed Forwarding the request to the upstream server failed. Please retry, and if the problem persists contact SaaS Manager support." You can ignore this message. it's displayed because the request was initiated from a direct URL outside SaaS Manager. We are working to improve the wording of this.
You can confirm that the application has been added by going to Enterprise applications in Azure.
Now that the application has been approved by an administrator, you can log in to SaaS Manager and connect using your non-admin account. To connect, go to the Integrations tab and search for Microsoft Entra ID. Select the Connect button.
Authorize additional scopes
If you want to authorize additional integration functionality, e.g. to enable deprovisioning, first select the three dots ⋮ and disconnect the integration, and then reconnect, selecting the features you want.
If you have previously consented to a set of scopes in Entra ID you may find that any additional scopes required (e.g. User.ReadWrite.All) are not correctly granted.
To resolve this, you may need to delete the SaaS Manager application in Entra ID and reconnect, to regrant the right scopes.
To delete the SaaS Manager application, find the Enterprise applications Azure service:
Then search for SaaS Manager (Microsoft Entra ID) (or SaaS Manager (Microsoft Azure AD), depending on when you set up the integration).
Select the application, then select Properties on the left-hand side and Delete the application.
Connect with Client Credentials
Please read this article on configuring Entra and connecting using Client Credentials.
Concealed user names in Microsoft 365 usage reports
By default, Microsoft 365 now anonymizes (or "conceals") user names in usage reports. If this setting is enabled, then SaaS Manager cannot read user-level usage data for Outlook, Teams, OneDrive or SharePoint.
If you want to see this then go to Settings > Org settings > Reports in the Microsoft 365 admin center.
IMPORTANT: Make sure that the checkbox for Display concealed user, group and site names in all reports is UNCHECKED.
The wording of this checkbox is very confusing - it's the opposite of what most people understand it to mean.
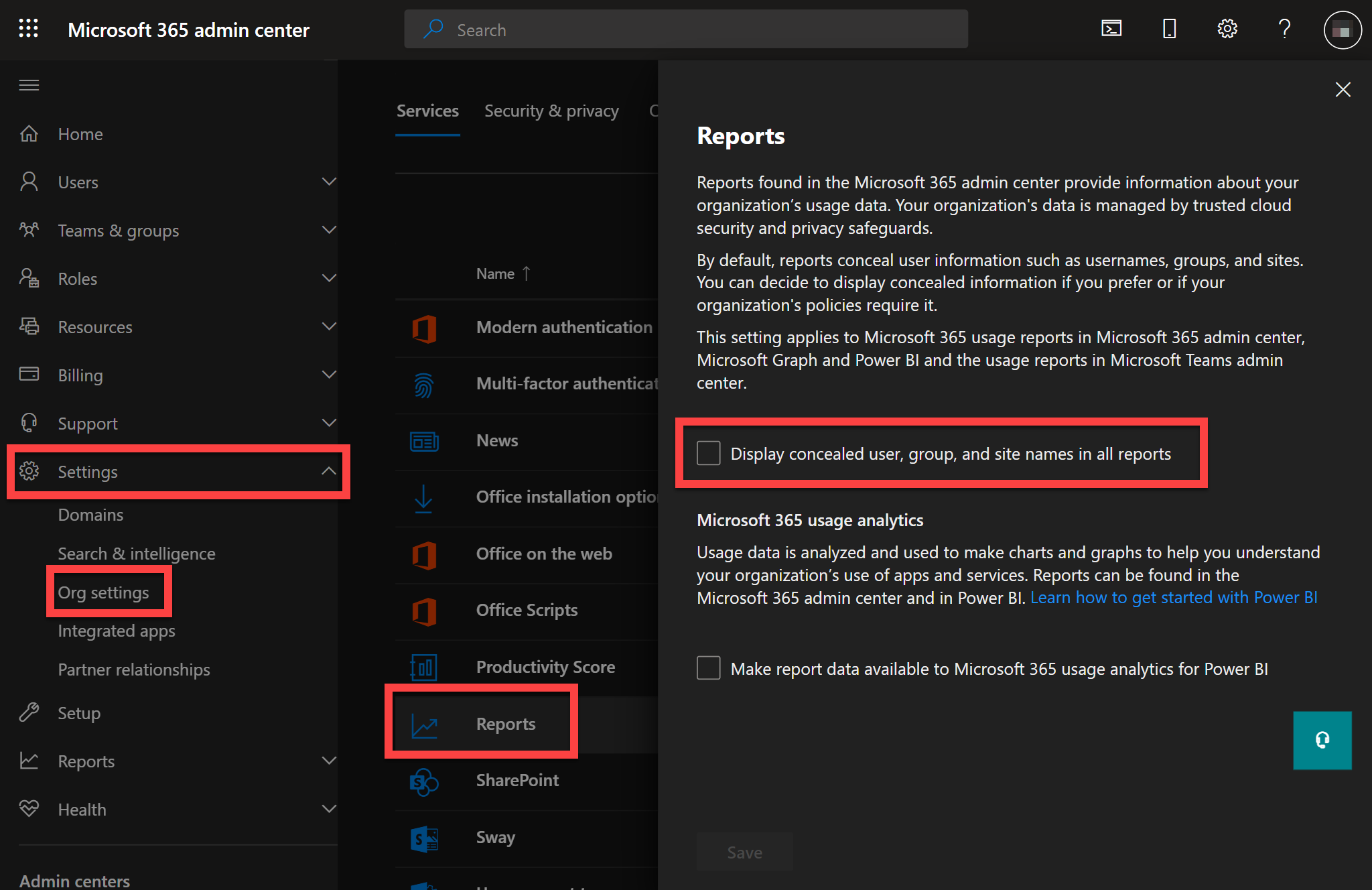
Select Save.
You must refresh the Microsoft 365 integration in SaaS Manager to update the data.
Microsoft 365 usage data for Outlook, Teams, OneDrive and SharePoint typically has a slight lag, so may not register usage from the previous 48 hours.
FAQs
How is the person type determined?
The person type is determined by the following logic:
- If the Entra ID User Type is set then it is mapped as follow:
- Guest => External
- Resource => Service account
- Member => Determined based off the Employee Type field (described in step 2).
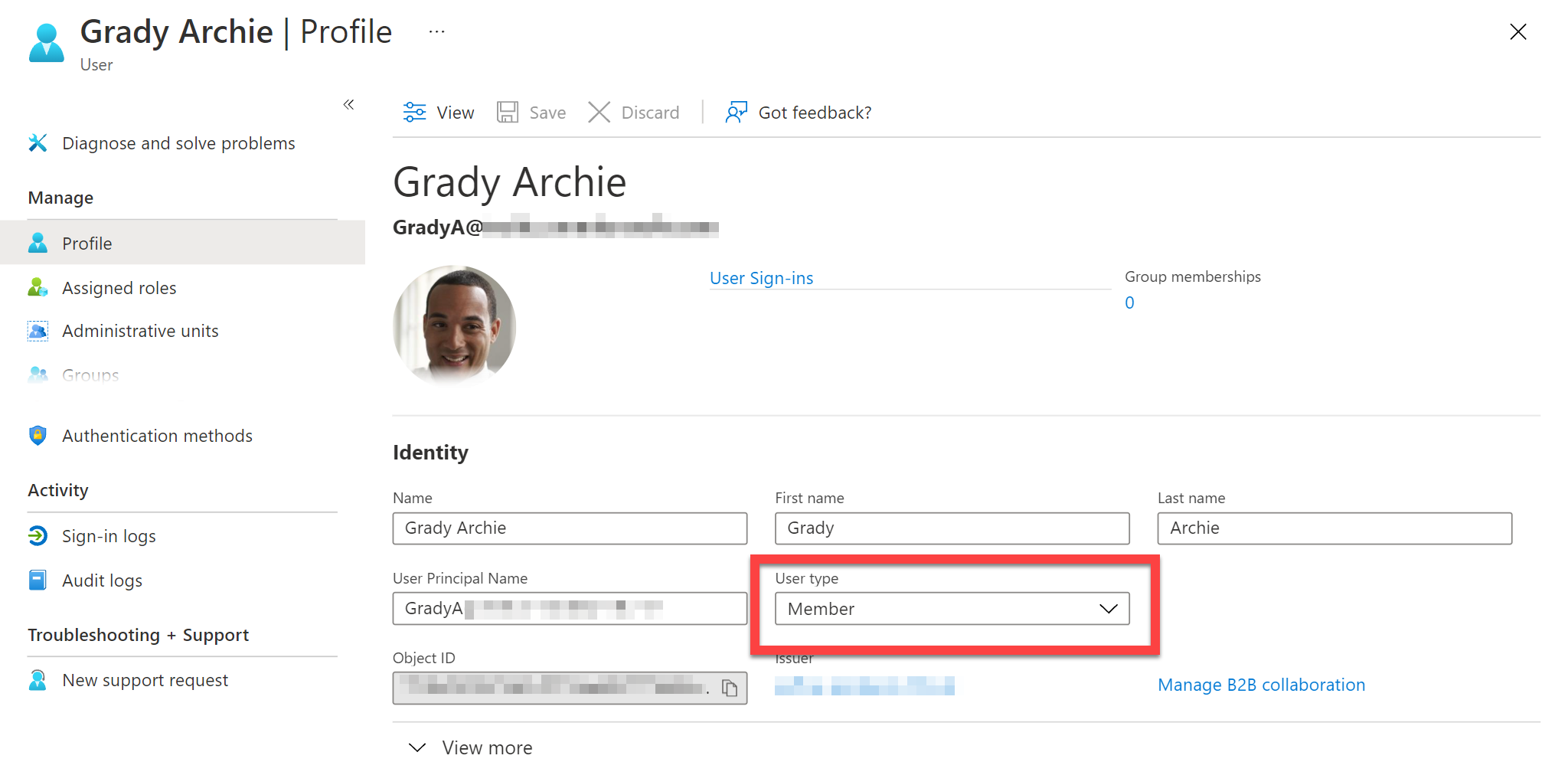
- If the Entra ID Employee Type field is set then it is mapped as follows:
- Employee => Employee
- Contractor => Contractor
- Consultant or Vendor => External
- If the Employee Type is not set, then the SaaS Manager person type mapping rules are used.
How is the email address determined?
The following attributes are checked in order, and the first of these is used as the primary email address for the user:
-
onPremisesUserPrincipalName(if set, and if a valid email address) -
userPrincipalName(if set, and if a valid email address) - based on identities assigned to the user, the first
issuerAssignedIdthat is also a valid email address - email
aliases -
proxyAddresseswith ansmtp:prefix
Other values are assigned as email aliases.
What user data is returned by Entra ID?
- Email address and aliases
- First name and last name
- Account enabled (the user is marked as Suspended if this is false)
- Employee ID
- Employee type
- Job title
- User department (used for the assigned team if Entra is the SaaS Manager team source
- Office location (mapped to the SaaS Manager location)
- Cost center
- Employee hire date (mapped to person Start date)
- Employee leaving date/time (mapped to person Terminated date)
- Manager
- Usage location
- Immutable ID
- User type: Guest (mapped to External person type) or Resource (mapped to Service account person type)
- Last device activity (if the
DeviceManagementManagedDevices.Read.Allscope is granted) - Last sign in date/time
- Extension attributes (optional)
- Company name (optional)
How do I import extension attribute data?
- Select Mappings from the 'more' menu for the integration
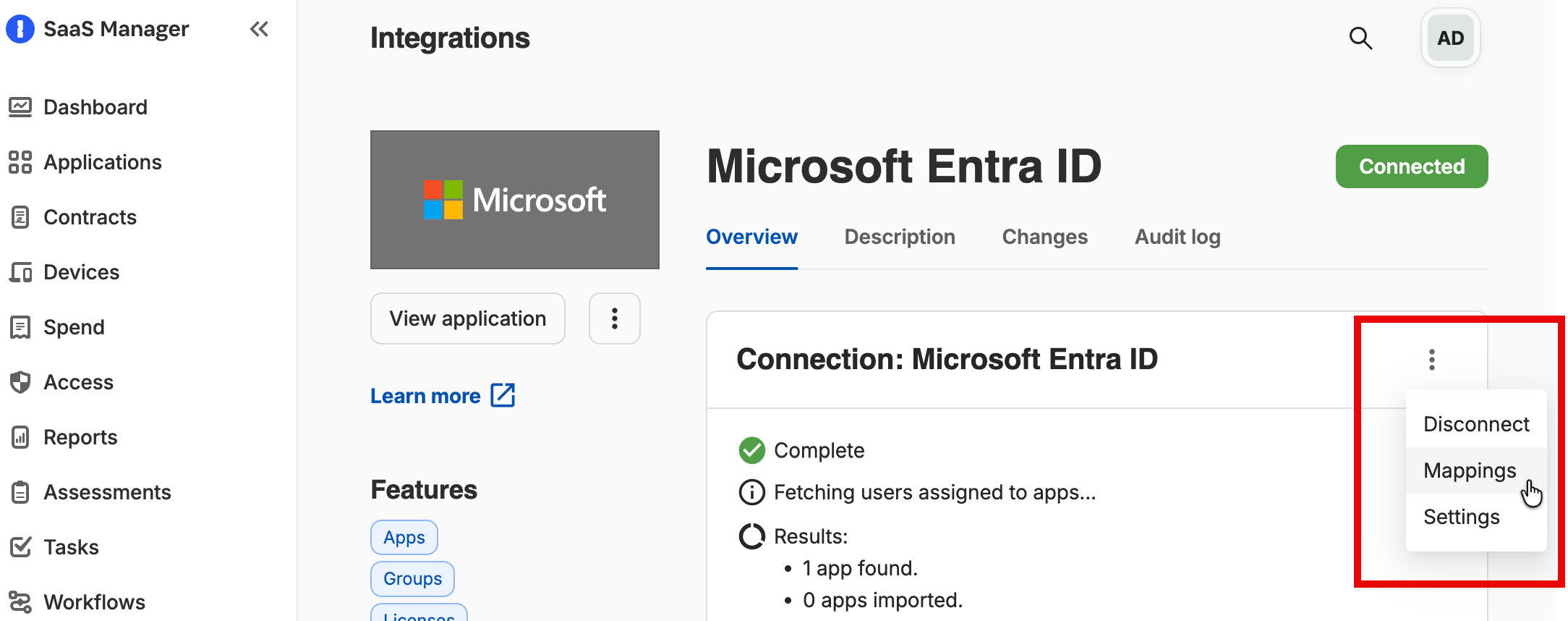
- Select Add mapping and choose the extension attributes you want to import.
How does SaaS Manager determine is SCIM is enabled for an Entra app?
SaaS Manager checks Entra for Add or Delete template rule mappings where synchronization jobs are enabled.
An application shows a 'High' OAuth Access Risk, but no users have a 'High' OAuth Access Risk
An Entra administrator can grant specific consents on behalf of all users. If this has been granted then SaaS Manager derives a risk rating from these consents and applies this to the application.
An application that I can see in the Entra ID Enterprise Applications list isn't showing in SaaS Manager
SaaS Manager only imports applications which meet one or more criteria:
- Application is configured for SAML2.
- Application has users or groups assigned to them.
- Entra ID has issued OAuth2 tokens for the application, and they are still valid.
What does the last login date for Microsoft 365 reflect?
If you have an Entra ID P1 or P2 license then SaaS Manager will retrieve the last interactive login date for your users. An interactive login is where a user actually enters a password (or uses an MFA app or biometric factor or QR code) to sign in to an application using their Entra ID account.
If users are primarily accessing Microsoft 365 through mobile apps (for example) then this may not reflect actual activity as these applications may be using non-interactive logins. Data relating to non-interactive logins is not available through Microsoft APIs.
To overcome this limitation, SaaS Manager combines Entra ID last login dates with Microsoft 365 usage data from Outlook, Teams, OneDrive and SharePoint. This gives a more accurate indication of last usage.
I logged in yesterday but SaaS Manager shows a last login from a few days ago?
Microsoft Activity report data lags by a day or two (based on Microsoft's design).
Microsoft say "The reports typically become available within 48 hours, but might sometimes take several days to become available". See https://learn.microsoft.com/en-us/microsoft-365/admin/activity-reports/activity-reports?view=o365-worldwide
What does the last login date for Teams or Outlook reflect?
Teams and Outlook usage data indicates the last time a user accessed Teams or Outlook, either on the web, from a desktop client, or from a mobile device. It does not reflect the last date a Teams meeting was held or an Outlook message was sent or received.
How do you offboard a person from Microsoft 365 with SaaS Manager?
The SaaS Manager integrations with Microsoft support a range of offboarding actions. For a guide on recommended use of those actions refer to Offboard users from Microsoft 365.
We have a hybrid environment with Entra and Active Directory — how does this affect my use of SaaS Manager?
SaaS Manager can’t connect directly to Active Directory (AD), since there is no API exposed over the internet to enable integration. However, you can still use SaaS Manager workflows to initiate PowerShell scripts that run in your local environment.
Group membership management depends on how your AD and Entra environments are synchronized:
-
Entra ID Connect (AD → Entra):
AD groups sync to Entra, but AD remains the source of authority. Membership changes must be made in AD, and SaaS Manager cannot modify these groups. -
Microsoft Entra Cloud Sync with Group Writeback (Entra → AD):
Entra cloud security groups are provisioned back into AD. In this case, Entra is the source of authority, and SaaS Manager can manage memberships for these groups via the Microsoft Graph API, as it would with Entra-only setups. Changes initiated by SaaS Manager will be synchronized back to AD.
These distinctions are particularly important to consider when thinking about configuration of SaaS Manager Access levels.
I'm getting the message "Insufficient privileges to complete the operation"
SaaS Manager can connect to Entra using either Auth Code flow ('delegated' permissions) or Client Credentials ('application' permissions). Both of these approaches use 'scopes' to determine the access SaaS Manager has to your Entra tenant. For Auth Code flow, these scopes are requested and granted to a specific user during connection; for Client Credentials the scopes are configured by your Entra administrator.
For Auth Code flow, a scope such as User.ReadWrite.All sounds like it will allow SaaS Manager to alter any aspect of a user's attributes, but Entra applies more fine-grained permissions depending on the role that the connecting user has versus the user being acted on.
This Microsoft table "Who can perform sensitive actions?" is a helpful reference to trouble-shooting this kind of error, particularly during deprovisioning actions. e.g. even a user with a "User admin" role cannot act upon a user with a custom role assigned.
Client Credentials can give you a way to configure more granular access, but bear in mind that some actions (such as resetting a user password as part of the Revoke access action) do not work with Client Credentials ('application' permissions).
Comments
0 comments
Please sign in to leave a comment.