This article shows you how to connect to Azure using client credentials. Use this if you have chosen to use client credentials when connecting Azure, or if you are using Azure in China (a service operated by 21 Vianet).
To configure the integration you must have Azure AD administrative access in order to create and configure a new App Registration
- Create credentials in Azure (an 'app')
- Connect 1Password SaaS Manager to your Azure tenant using these credentials.
Register the app
- Login to https://portal.azure.com/ (for Microsoft Entra ID) or https://portal.azure.cn/ (for Azure in China)
- Find App registrations:
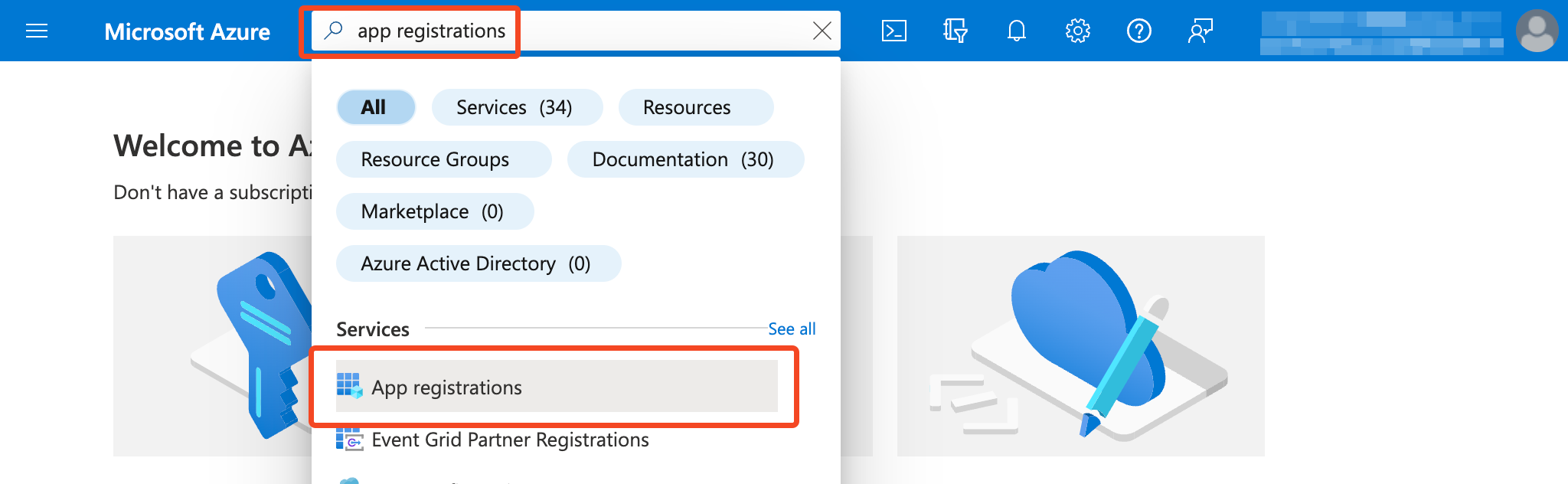
- Click New registration.
- Enter a name (e.g.
SaaS Manager) - Choose Accounts in this organizational directory only (Single tenant)
- You do not need to enter a Redirect URI - just click Register to continue.
Configuring API permissions
-
- On the API permissions tab, click Add a permission

- Under the Microsoft APIs tab choose Microsoft Graph:
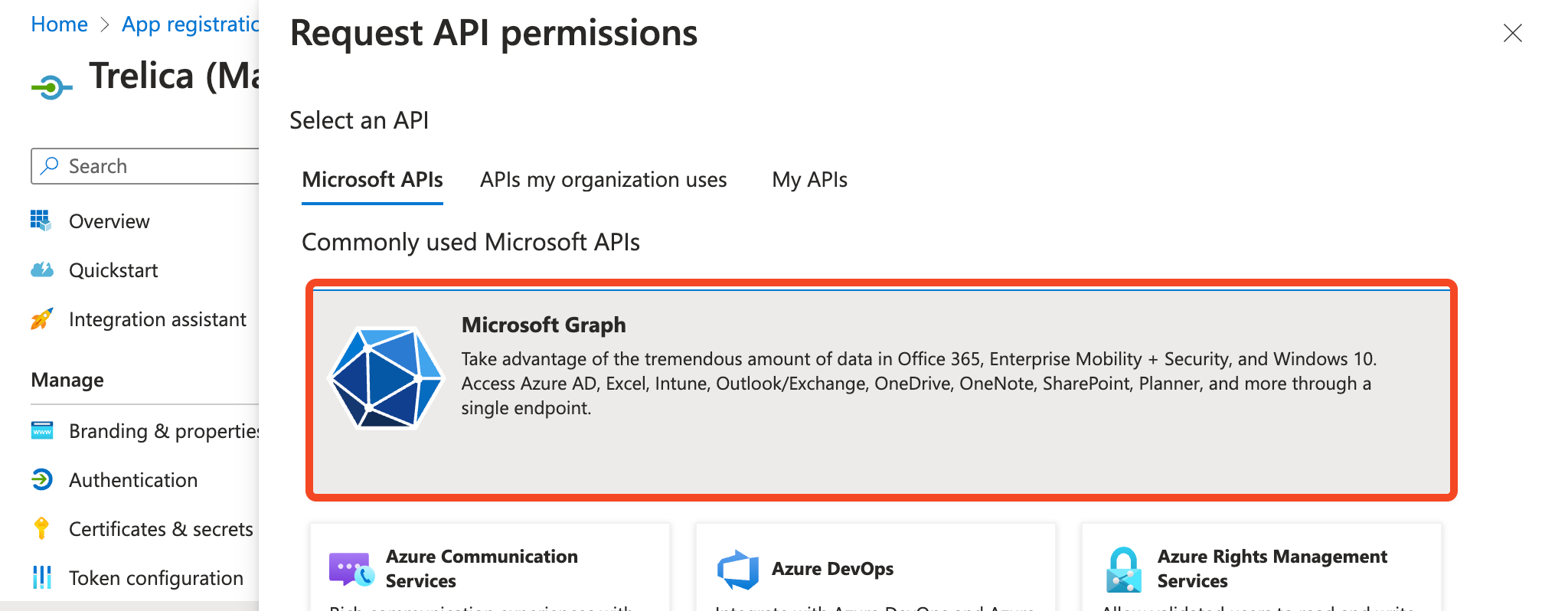
-
Choose Application permissions search for each of the scopes in the table below and tick them, depending on the features you require:
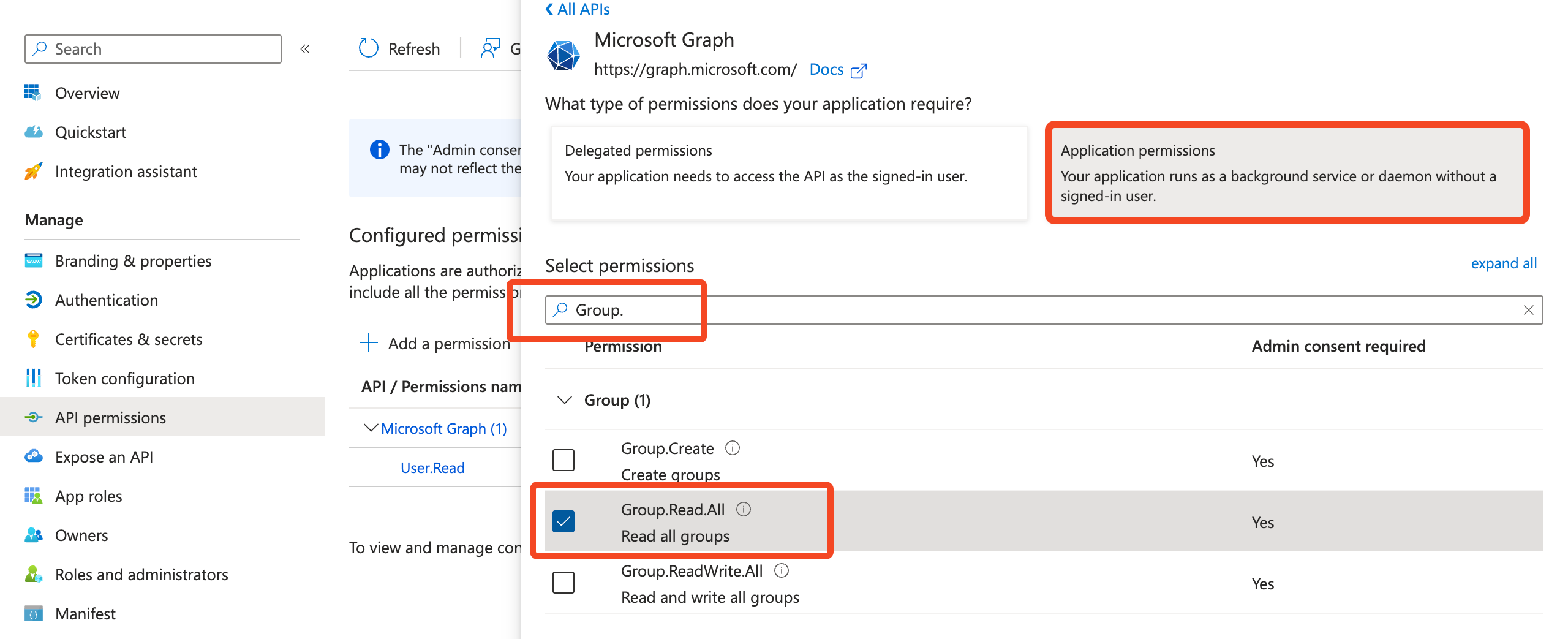 Please double-check that you have chosen the Application permissions box and not Delegated permissions before selecting permissions.
Please double-check that you have chosen the Application permissions box and not Delegated permissions before selecting permissions.Core scopes Application.Read.AllRead applications and service principals. RoleManagement.Read.DirectoryRead directory role templates, directory roles, and memberships. Synchronization.Read.AllRead all Azure AD SCIM synchronization data. Used to understand if Azure is configured to provision and deprovision users for apps. Group.Read.AllRead groups. GroupMember.Read.AllRead the memberships of groups. Directory.Read.AllRequired to read OAuth token permissions. The integration will work without this but won't return data about OAuth logins. User.Read.AllRead the full set of profile properties including managers of users in your organization. AuditLog.Read.AllRead all audit log data. DeviceManagementManagedDevices.Read.AllRead the properties of devices managed by Microsoft Intune. Reports.Read.AllRead Microsoft365 usage reports. LicenseAssignment.Read.AllRead license assignments for all users. AppRoleAssignment.ReadWrite.AllAllows the app to manage user and app role assignments. ReadWrite is the minimum scope required, although SaaS Manager does not write app role assignments. IdentityProvider.Read.AllRead all identity providers. Used to return verified domains. Organization.Read.AllRead the organization and related resources. Used to return the tenant ID and name. Deprovisioning User.ReadWrite.AllUpdate the profile of every user in the organization GroupMember.ReadWrite.AllRead and write group memberships UserAuthenticationMethod.ReadWrite.AllRead and write users' authentication methods Provisioning (additional to Deprovisioning scopes) RoleManagement.ReadWrite.DirectoryRead and write directory RBAC settings - Click Add permissions
- Finally, click Grant admin consent:

- On the API permissions tab, click Add a permission
Create a new secret
- Go to Certificates & secrets
- Click New client secret
- Give the secret a name (e.g.
SaaS Manager) and chose the Expiry duration that you are comfortable with (we recommend 12 or 24 months). - Click Add
Collecting the IDs you need
You need three IDs which you can copy from Azure.cn:
-
From the Certificates & secrets tab copy the Client Secret Value (not the Secret ID)
The Client Secret Value will only be available for you to copy for a short period of time. If you are unable to view or copy it, then create new one.
- From the Overview tab copy the Application (client ID) and the Directory (tenant) ID
Connect from SaaS Manager
- In SaaS Manager, go to Integrations and choose either Azure in China or Microsoft Entra ID.
- Click Connect and enter the IDs that you gathered earlier.
- Click Connect again.
- The integration will run in the background.
Comments
0 comments
Please sign in to leave a comment.