Scopes requested
1Password SaaS Manager needs theDeviceManagementManagedDevices.Read.All scope to read Intune device data.
Application consent in Entra ID
Microsoft Entra ID (formerly Azure AD) now offers a very comprehensive approach to OAuth application security. Recommended settings are to limit users' abilities to consent to OAuth applications - if you're an Entra Administrator you can see the configuration your organization is using under Enterprise applications > Consent and permissions > User consent settings.
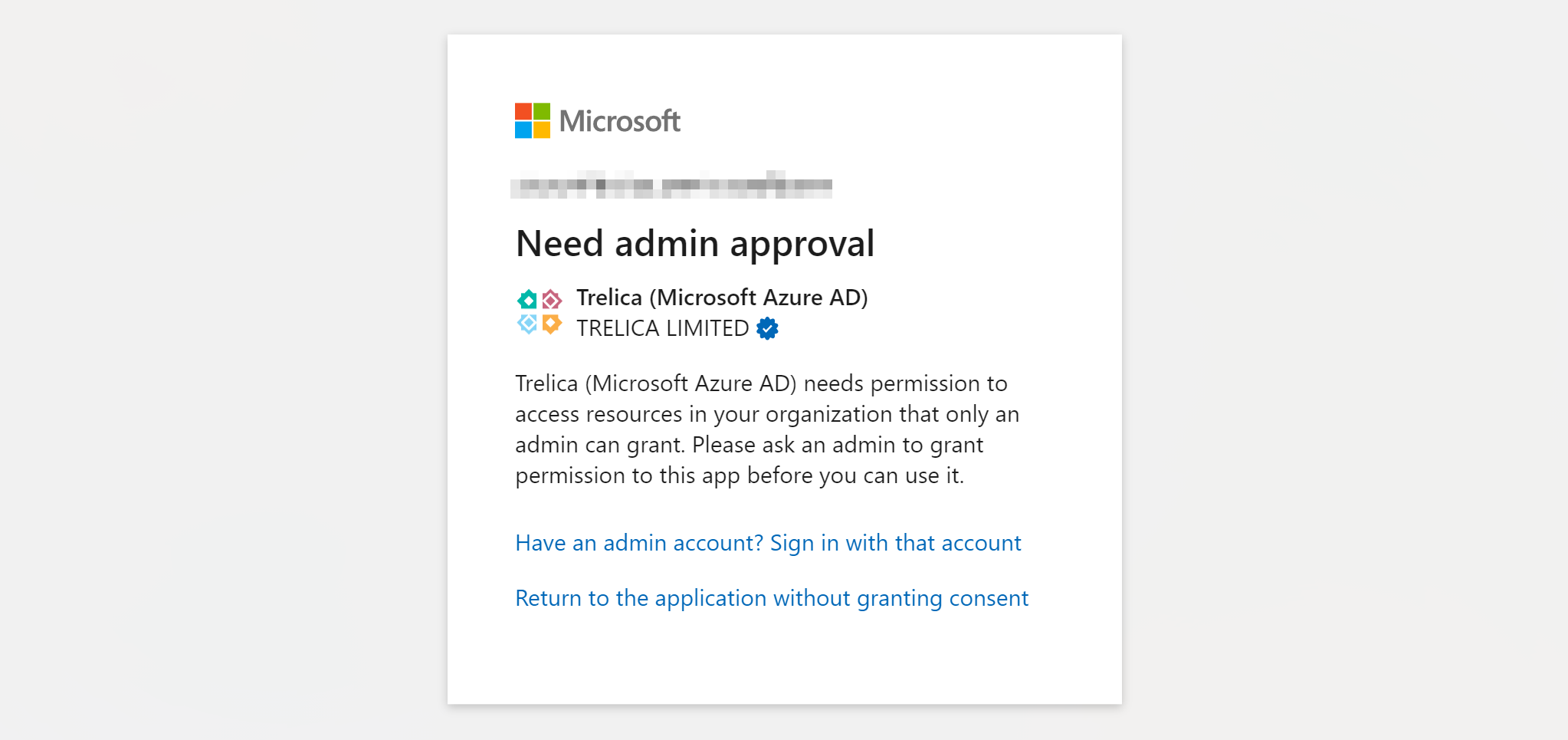
SaaS Manager requires a number of permissions to access resources in Entra ID and it's likely you will have Do not allow user consent or Allow user consent for apps from verified publishers, for selected permissions selected. In this case connecting SaaS Manager to Entra ID with a non-Entra administrator account will show the Need admin approval message:
As the message suggests, you could switch to using an Entra administrator account to make the connection by clicking Have an admin account? Sign in with that account.
SaaS Manager will not be granted the full access of your administrator account - our access is limited to the OAuth scopes we request.
Approving the SaaS Manager application connection using a separate Entra admin account
If you want to use a different user account (perhaps a specific SaaS Manager 'service' account with just the Global Reader role) to connect from SaaS Manager to Entra ID, then you will still need an Entra Administrator to approve the SaaS Manager application.
The easiest way to do this is to ask an Entra Admin (who does not need to have a SaaS Manager account) to click the following link:
This will initiate the process for approving the SaaS Manager connection in Entra ID.
You do NOT need to Consent on behalf of your organization. If you leave the box unchecked it just means that if a new connection is made, then the user must review the access SaaS Manager is requesting.
After you click Accept, then the user will see a message from SaaS Manager that says "Request forwarding failed Forwarding the request to the upstream server failed. Please retry, and if the problem persists contact SaaS Manager support."
You can ignore this message - it's simply because the request was initiated from a direct URL outside SaaS Manager. We are working to improve the wording of this.
Assigning and removing devices from Azure AD groups
The Microsoft Intune integration uses a normal OAuth consent process.
However, assigning and removing devices from Azure AD groups requires 'Application' rather than 'Delegated' Azure API permissions for the Device.ReadWrite.All scope (which is required for setting group membership). This means that an application must be created and configured directly in your Entra ID tenant.
There are two parts to configuring the connection - you may need help from an IT admin to complete the first step.
- Create credentials in Entra ID (an 'app')
- Connect SaaS Manager to Microsoft 365 using these credentials.
Register the app
- Login to Entra ID and find App registrations:
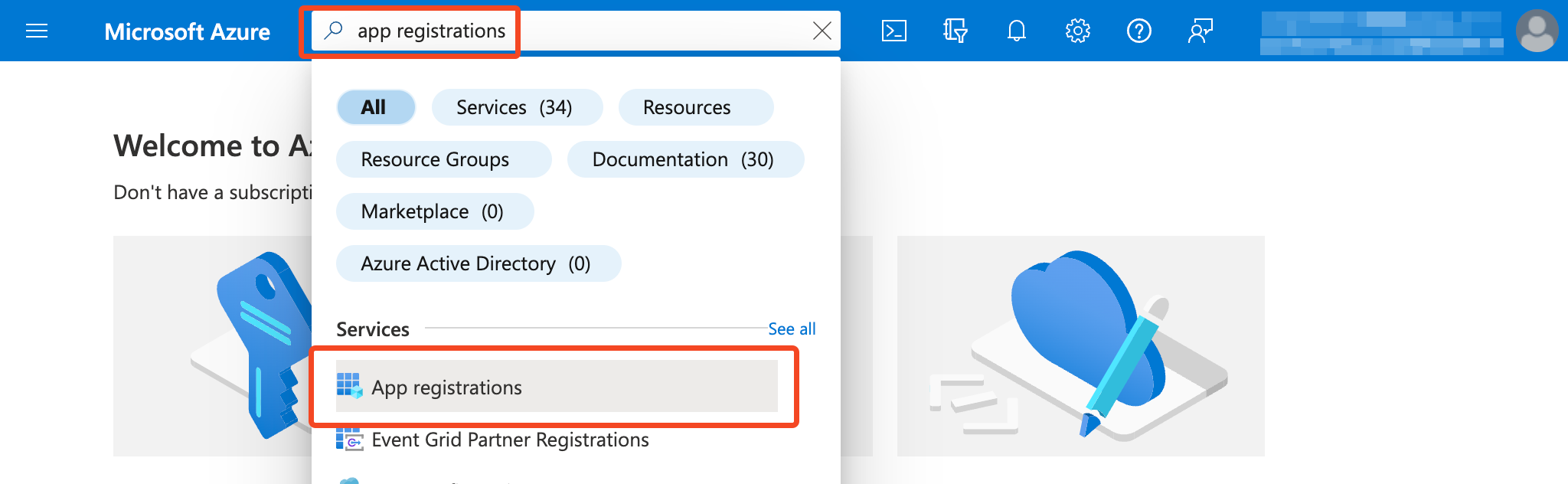
- Click New registration.
- Enter a name (e.g.
SaaS Manager (Intune)) - Under "Supported account types", select Accounts in this organizational directory only (Single tenant).
- You do not need to enter a Redirect URI. Select Register to continue.
Configuring API permissions
- On the API permissions tab, click Add a permission
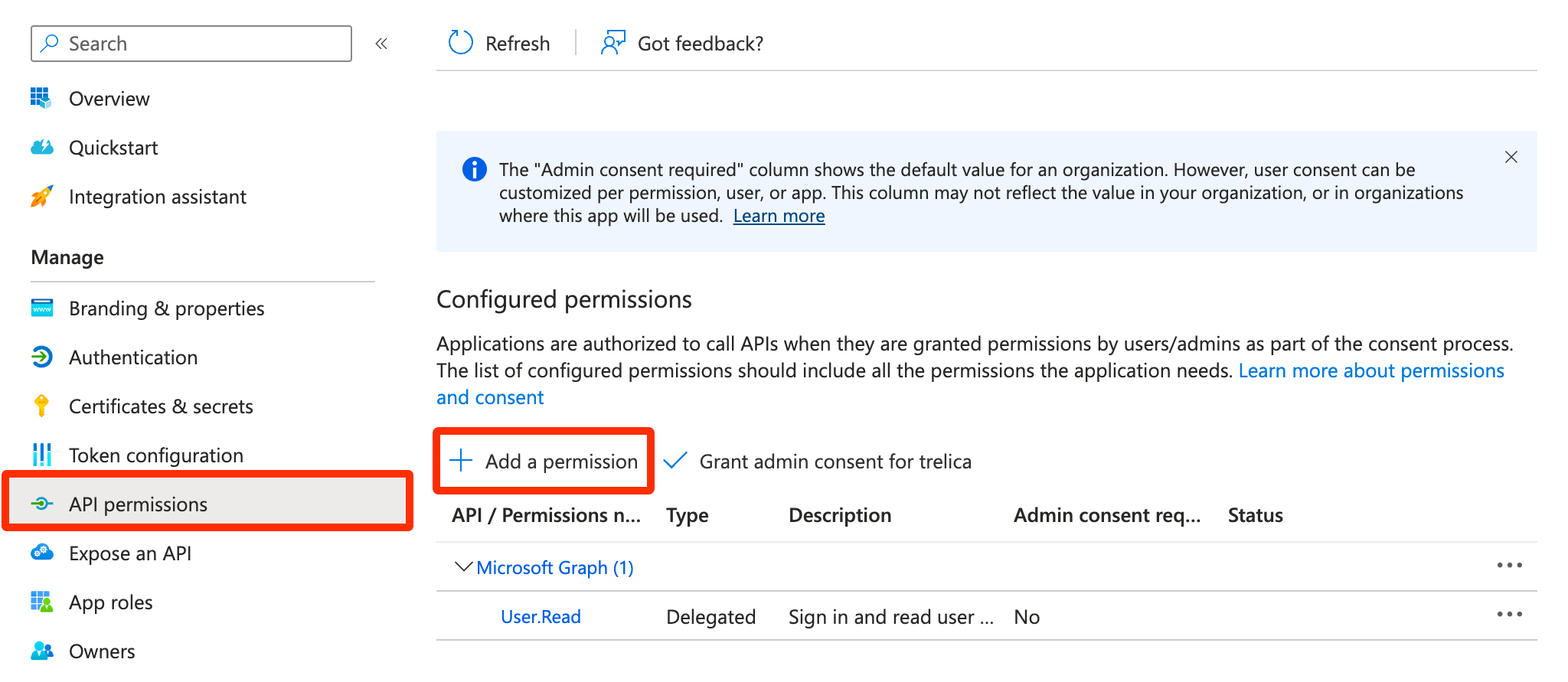
- Under the Microsoft APIs tab select Microsoft Graph.
-
Select Application permissions then search for
Group.Read.Alland select it. Do the same for
Do the same for GroupMember.ReadWrite.AllDevice.ReadWrite.AllandDeviceManagementManagedDevices.Read.All. - Click Add permissions.
- Finally, click Grant admin consent.
Create a new secret
- Go to Certificates & secrets
- Click New client secret
- Give the secret a name (e.g.
SaaS Manager) and chose the Expiry duration that you are comfortable with (we recommend 12 or 24 months).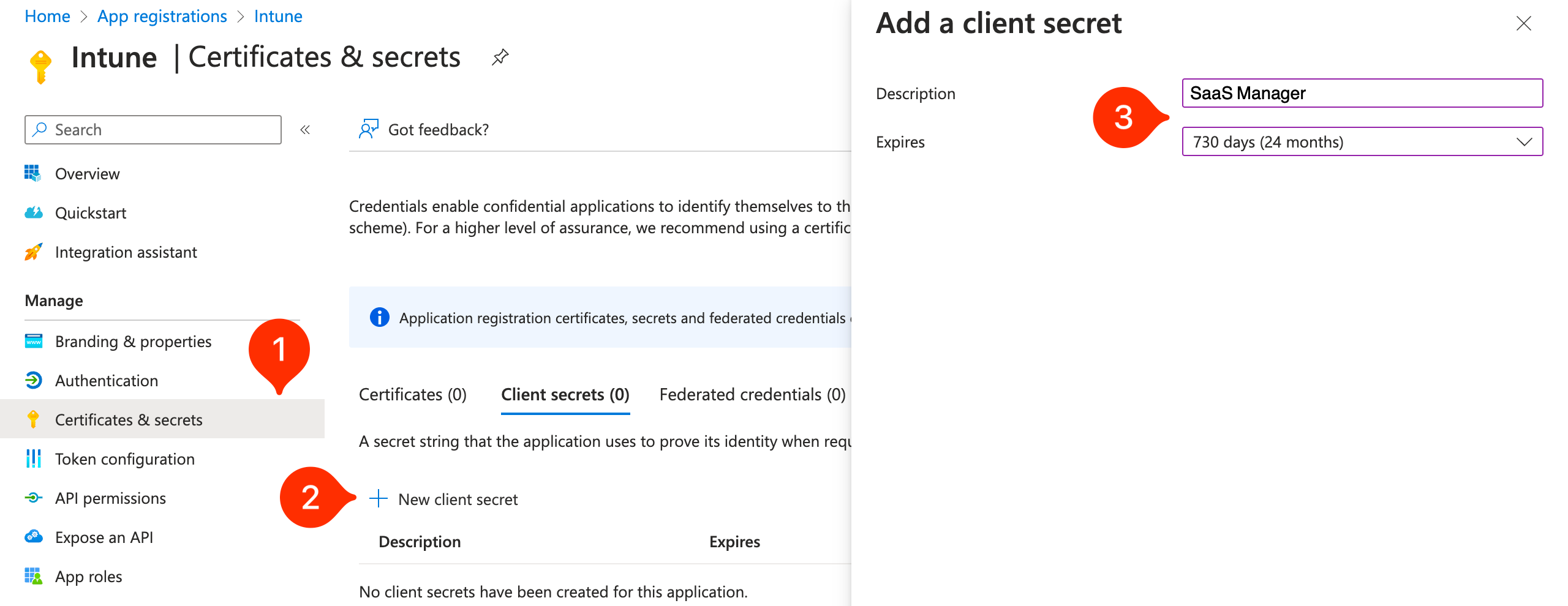
- Click Add
Collecting the IDs you need
You need three IDs which you can copy from Entra ID:
-
From the Certificates & secrets tab copy the Client Secret Value (not the Secret ID)

The Client secret value will only be available for you to copy for a short period of time. If you are unable to view or copy it, then just create new one.
- From the Overview tab copy the Application (client ID) and the Directory (tenant) ID.
Connect from SaaS Manager
- In SaaS Manager, go to Integrations > Microsoft Intune.
- Click Connect and enter the IDs that you gathered earlier.
- Click Connect again.
- You may need to login and consent to other scopes (required for other Intune actions).
- The integration will run in the background.
Comments
0 comments
Please sign in to leave a comment.